Model-based threat analysis
Model-based threat analysis is a threat modelling [MTA1, MTA2, MTA3, MTA4] approach that utilizes STRIDE [MTA2] as a basis. It serves as means to analyse systems for threats as well as failures [MTA1], and consists of three major components [MTA3]:
- A system model represents the system under consideration in its current status. This means that the approach can be applied during the design phase where assumptions about the future system are driving development, as well as during the implementation phase which reveals shortcomings of the planned system and therefore results in an adaption of the system. Moreover, model-based threat analysis can also be applied during the operational phase when the system is already running. A component may fail and, therefore, requires The system model is based on a data flow diagram [MTA4]. It holds all known security attributes of system components as well as the connections between them. [MTA3]
- A threat model represents a digital twin of known threats. It is constituted of rules that allow for a later analysis of the system model. These rules are anti-patterns, which are basically system configurations that are considered insecure and should therefore not be contained within the system under consideration. [MTA3]
- A threat analysis engine enables an automated analysis of the system. It compares each rule with the system model to detect potentially insecure configurations and consequently threats the system under consideration may be affected by.
The whole threat modelling process results in a catalogue depicting threats that the system suffers from and, consequently, require treatment [MTA3]. This is supported by including the STRIDE [MTA2] category, as well as impact and attack feasibility of the threat [MTA5]. The current rule sets were derived from UNECE WP29, ETSI and the ITU.
The described approach is an iterative process which allows for consecutive analysis of the system with applied security measures that serve as threat mitigations (see Figure below).
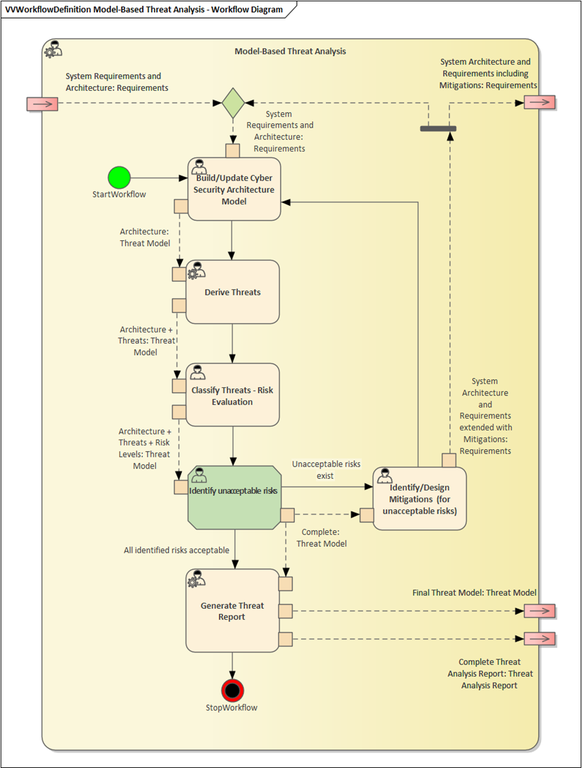
- Potential threats can be automatically detected
- Can be applied during the whole system lifecycle
- Predefined impact and attack feasibility inform decisions for the risk treatment process
- Needs a structural model of the system
- Requires a rule set for the target domain
- [MTA1] C. Schmittner, S. Chlup, A. Fellner, G. Macher, E. Brenner, ThreatGet: Threat modeling based approach for automated and connected vehicle systems, AmE 2020 - Automotive meets Electronics; 11th GMM-Symposium, March 2020
- [MTA2] A. Shostack, Threat modeling: designing for security, Wiley, 2014
- [MTA3] C. Schmittner, P. Tummeltshammer, D. Hofbauer, A. Shaaban, M. Meidlinger, M. Tauber, A. Bonitz, R. Hametner, M. Brandstetter, Threat Modeling in the Railway Domain, January 2019
- [MTA4] P. Torr, Demystifying the Threat-Modeling Process, IEEE Security and PRivacy Magazine, September 2005
- [MTA5] ISO/TC 22/SC 32, ISO/SAE DIS 21434 Road vehicles — Cybersecurity engineering, ISO – International Standardization Organization, May 2020
