Risk Analysis
In technical domains, risk is generally defined as the probability of damage including the severity of the considered damage, while Risk Assessment is a fundamental decision-making process in the development of information security, resulting in the selection of appropriate safeguards for an information system. Risk analysis is, indeed, the first step of the Risk Assessment process in which the system should be properly modelled as well as the potential threats.
There are several methods for assessing risk, from checklists and questionnaires to algorithms and software tools. The choice of the Risk Analysis methodology should be taken on the basis of several factors, such as cost, complexity, completeness, feasibility, level of automation etc [RAS1].
According to [RAS1], Risk Analysis methodologies can be classified at a high-level following these two criteria: deterministic vs stochastic, quantitative vs qualitative vs hybrid.
Beside the previous classification, methodologies developed during recent years can be defined also as:
- Scenario-based vs asset-threat-vulnerability (ATV) approach: in scenario-based analysis risk scenarios are identified a priori, while in ATV methodologies risk scenarios are a consequence of the assets, threats and vulnerabilities defined;
- Cross-sectorial, when the methodology could be applied to several domains according to definition provided in [RAS2], or single-sectorial, when the methodology could be applied only in a specific sector.
Quantitative Risk analysis indeed should be preferred when it comes the evaluation of a complex system with high safety standards, since it is more reliable and not affected by subjective judgment.
One of the main challenges to address in the quantitative Risk Analysis is the scarcity of data, which makes it difficult to use probabilistic techniques to foresee risks and potential consequences. To solve this issue efforts have been spent in two ways: on one hand the research and analysis of existing dataset provided by official international organisation, such as Global Terrorism Database (GTD) [RAS4] for terrorism and Major Accidents Reporting System (eMARS) for industrial incidents[RAS5], has been carried out, while on the other hand Artificial Intelligence techniques, such as Neural Network, or Bayesian approaches have been applied to overcome the data gap.
Another challenging issue is the modelling of multi-hazard risk, i.e. when the risk is generated by a set of hazards which can occur together or in sequence, namely cascading effect. Indeed, the manifestation of various threats, either jointly or very close in time, is an eventuality that must be considered in order to perform an exhaustive risk analysis for a given system. It is possible dealing with this task in two different ways: considering the events as independent or introducing a relation among the threats. The first approach is the most diffused and the easiest one, because less data and a smaller number of calculations are needed. However, assuming the independence of the hazards leads to a reduction of information and to a less accurate model. For this reason, evaluating the correlations among events is the best practice, even if it is more expensive in terms of modelling and requires much information [RAS6].
Within VALU3S project, the Risk Analysis chosen to deal with complex electronic and automated systems is:
- Quantitative: to provide reliable, objective and measurable outputs;
- Deterministic: to provide exact values for outputs;
- ATV approach-based: to generate risk scenario starting from the knowledge of the system;
- Cross-sectorial: to be applied in different domains.
The considered risk analysis method generally takes the following steps:
- Generation of attack/incident scenarios according to system structure and components;
- Simulation of attack/incident scenarios and intervention of safety countermeasures to generate scenario outcomes (e.g. attack prevented, defused, mitigated or not mitigated);
- Computation of outcomes likelihood;
- Computation of outcomes impact;
- Computation of outcomes risk.
The methodology is flexible because the generation of scenarios is performed according to the initial system modelling. This feature allows to apply the methodology to different systems, regardless of their peculiarities and interdependencies. On the other hand, this approach cannot allow a detailed modelling of system components.
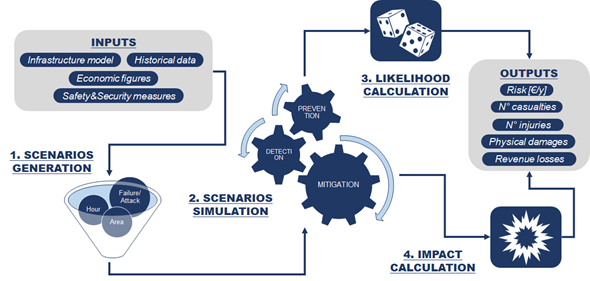
The inputs needed by the algorithm (Figure 3.11) to perform a scenario-based cross-sectorial quantitative risk analysis are the following:
- A data model of the infrastructure (or system considered), e.g. which components are present;
- Historical data, e.g. data on past incident/attacks for systems similar to the one under consideration;
- Economic figures, such as the monetary values of system components;
- Safety and security measures which are present in the system.
The outputs of the scenario-based cross-sectorial quantitative risk analysis are the following:
- Risk level of each component of the system, expressed as €/year, according to each scenario;
- The likelihood of each scenario generated;
- Number of casualties and injuries due to attacks/incidents for each scenario;
- An estimation of the percentage physical damage to system components due to attacks/incidents for each scenario;
- The economic losses due to the impact of attack/incidents for each scenario;
- Generation and analysis of thousands of attack/incident scenarios;
- Quantitative outputs which can measure the risk level of the system in an objective manner;
- Flexibility to be applied on different systems;
- Need of a large input dataset, including a precise modelling of the infrastructure;
- Interdependencies among system components modelled only at high level.
- [RAS1] Lichtenstein, S. (1996) "Factors in the selection of a risk assessment method", Information Management & Computer Security, Vol. 4, No. 4, 20-25, MCB University Press, U.K.
- [RAS2] Jérôme Tixier, Gilles Dusserre, Olivier Salvi, Didier Gaston. Review of 62 risk analysis methodologies of industrial plants: review. Journal of Loss Prevention in the Process Industries, Elsevier, 2002, 15 (4), pp.291-303. ff10.1016/S0950-4230(02)00008-6ff. ffineris-00961858f 1
- [RAS3] European Risk Assessment and Contingency, EURACOM, Grant Agreement: 225579 Seventh Framework Programme Theme ICT-SEC-2007-7.0-0
- [RAS4] Global Terrorism Database, https://start.umd.edu/gtd/
- [RAS5] eMars Database, https://emars.jrc.ec.europa.eu/en/emars/content
- [RAS6] Pasino A., Clematis A., Battista U., De Angeli S., Ottonello D. (2020) “A review of single and multi-hazard risk assessment approaches for critical infrastructures protection”, 2nd Scientific International Conference on CBRNe SICC Series
