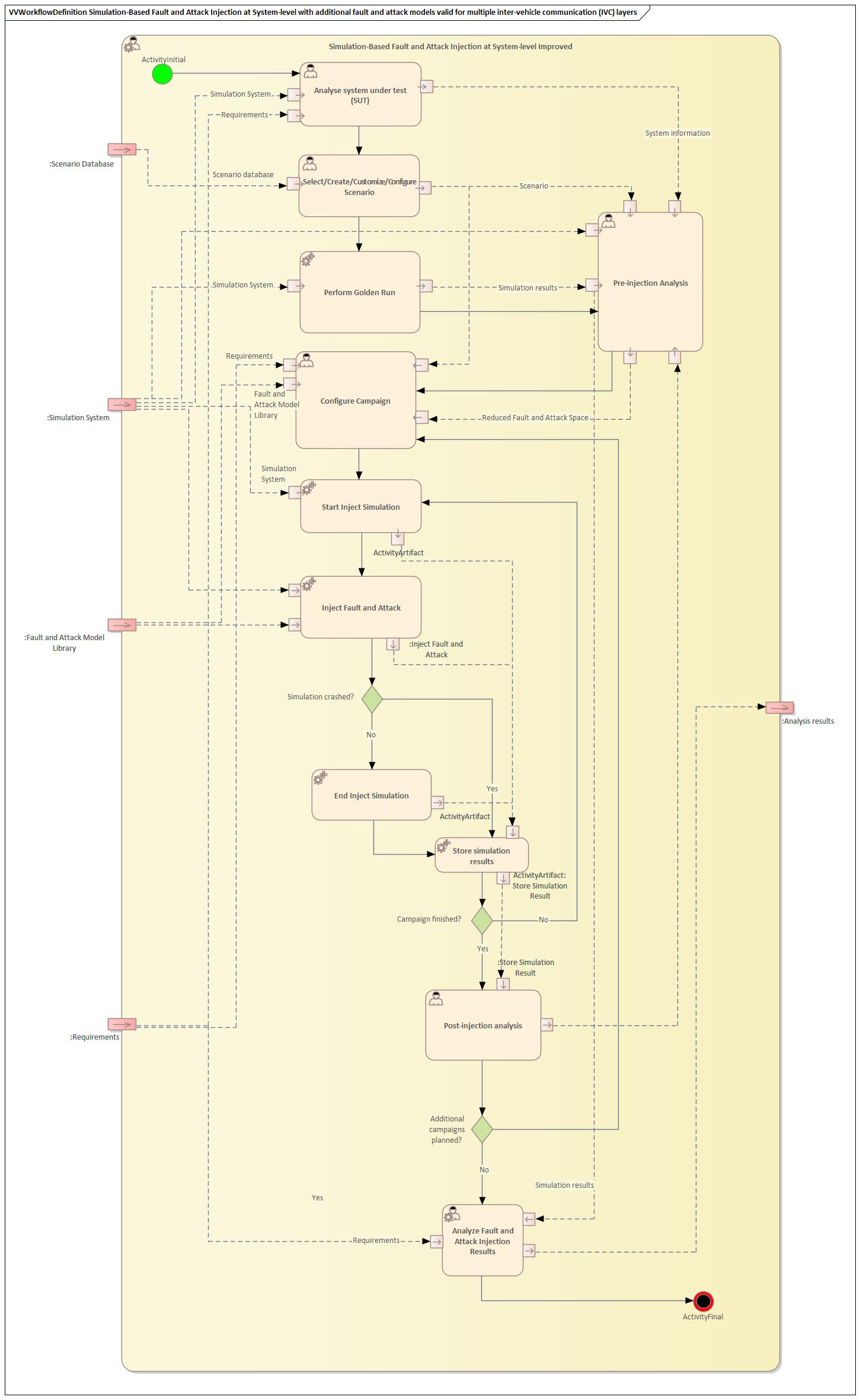
Simulation-Based Fault and Attack Injection at System-level
The Simulation-Based Fault and Attack Injection at System-level workflow describes the application of the V&V methods SFI (Simulation-based fault injection at system level) and SAI (Simulation-based attack injection at system level). These methods allow fault- and attack injections into simulated target communication system models to evaluate the impact of faults and cybersecurity attacks on target systems at early development phases.