Vulnerability Analysis of Cryptographic Modules Against Hardware-Based Attacks
One of the basic principles of cryptography is that according to Kerckhoff’s hypothesis [VAC1], it is assumed that the overall security of any cryptosystem is completely dependent on the security of the key, and that all other parameters of the crypto system are publicly observable. Thus, the cryptographic algorithms are assumed as open as long as the key generation scheme is not secure. In real life, many systems actually use well-known symmetric and asymmetric cryptographic algorithms (AES, 3DES, RSA, ECDSA, SHA) which have been applied in many domains and all experts are aware of their strengths and weaknesses.
Vulnerability analysis is complementary to cryptography. The robustness of a crypto system depends on the key used, or in other words, the attacker’s ability to predict the key. The hardware-based vulnerability analysis of key generation relies on 4 steps (Figure 3.12):
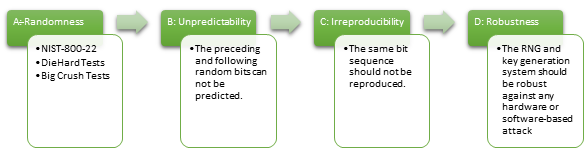
A: Randomness: There are two basic types of generators used to produce random sequences: true random number generators (TRNGs) and pseudorandom number generators (PRNGs) [VAC2]. TRNGs generate random numbers from a physical process (thermal noise, the photoelectric effect, ring oscillator) rather than by means of an algorithm. While TRNGs take the advantage of non-deterministic entropy sources, PRNGs generate bits in a deterministic manner. The PRNG-generated sequence is not truly random, because it is completely determined by an initial value, called the PRNG's seed (which may include truly random values). PRNGs tend to benefit from the external source of randomness (e.g., mouse movements, delay between keyboard presses etc.) which are practical in use but predictable either. In other words, an attacker can easily guess the outputs of a PRNG by applying statistical or machine learning methods so that the cryptographic keys or secrets (which uses the bit streams as outputs of PRNGs) also become guessable (the previous or next bits can be predicted). The first thing to apply for the vulnerability analysis of a cryptosystem is to check whether the system relies on a hardware-based RNG or not. Then, this RNG should be TRNG. To meet the true randomness criteria, three test suites are applied on a sufficient length of bit sequences: I) NIST-800-22 Randomness Test Suite [VAC3]; II) DieHard Test Suite [VAC4]; III) Big Crush Test Suite [VAC5]
The typical outputs of a TRNG must pass all 15 criteria of NIST-800-22 Randomness Test Suite which are listed as: i) Frequency (Monobit) ; ii) Frequency Test within a Block; iii) Runs; iv) Longest-Run-of-Ones in a Block; v) Binary Matrix Rank; vi) Discrete Fourier Transform (Spectral); vii) Non-overlapping Template Matching; viii) Overlapping Template Matching; ix) Maurer's "Universal Statistical"; x) Linear Complexity; xi) Serial ; xii) Approximate Entropy; xiii) Cumulative Sums (Cusums); xiv) Random Excursions; xv) Random Excursions Variant. Diehard and Big Crush Test Suites also cover additional criteria that should be met to evaluate the randomness.
B. Unpredictability: The randomness test suites [VAC3-5] are useful but the main message given by these tests is that the tested sequence is NOT random. As they rely on statistical techniques the randomness test suites do not give any guarantee about the true randomness of a bit sequence. Even if a bit sequence fulfils all the randomness test suites, they cannot present any quantification about their predictability. In order to say that a TRNG is reliable, the preceding and following random bits generated by the TRNG cannot be predicted by any technique. Although there exist alternative methods, the proposed predictability analysis was presented in [VAC6].
An ideal entropy source which is used as the core of a TRNG based on thresholding random noise should have constant power spectral density over its operating bandwidth. The proposed vulnerability analysis technique in VALU3S relies on the generation of independent and uniformly distributed bits, per-sample joint entropy of the generated bit sequence and the autocorrelation function of the output (also addressed in [VAC6]). Here, it is assumed that the underlying noise waveform is a continuous-time wide sense stationary Gaussian process, of which power spectral density is flat between two known frequencies. Given a continuous time wide-sense stationary flat band-limited Gaussian noise source, the test aims to investigate the necessary and sufficient conditions for generating independent and identically distributed random bits with uniform marginal probabilities via uniformly sampling from this process and providing analytical and numerical results for the per-sample joint entropy. This is realised by preparing an equivalent setup in place of the original one in order to make the derivations simpler.
C: Irreproducibility & D: Robustness: The strength of a crypto system almost depends on the strength of the key used or in other words on the difficulty for an attacker not only to predict the key but also assure the irreproducibility of the same bit sequence and recommend a robust design against attacks. The TRNGs should not rely on the deterministic sources, otherwise one can even predict the secret parameters of RNGs [VAC7]. In recent years, the majority of the TRNGs rely on non-linear systems, e.g. chaotic RNGs. So, in C and D, the vulnerability analysis of the TRNG is tackled so that the irreproducibility and robustness against attacks is jointly encountered.
This is realised by a novel predicting system (as addressed in [VAC6-9]) that is proposed to find out the security weaknesses of a chaotic RNG. Convergence of the predicting system is proved using auto-synchronization. Secret parameter of the target chaotic RNG is revealed where the public information is the design of the chaotic RNG and a scalar time series observed from the target chaotic system. Simulation and numerical results verifying the feasibility of the predicting system are also given similar to the recent papers of ERARGE [VAC8, VAC7, VAC9] such that next bit can be predicted as well while the same output bit sequence of the chaotic RNG can be regenerated.
- The proposed test covers not only one test suite but also a combination of three methods (NIST-800-22, DieHard, BigCrush). By doing so, the randomness analysis, when applied, will not miss any vulnerability related to true randomness which is a critical obligation to generate private cryptographic keys. The vulnerability analysis method is a strong methodology to verify and validate the cryptographic key generation which is an indispensable component for the end-to-end security of any cyber-physical smart system. It is strong because of two reasons: first it relies on hardware-based techniques so that it is not PRNG; second it does not address only the randomness of the bit sequence (generated by a RNG) but also its unpredictability, irreproducibility and the robustness (combined).
- The presented technique (within the context of VALU3S) can also be used to contribute to the privacy preservation as it prevents the leakage of any confidential information within/from the cyber-physical system components.
- The analysis and tests that relies on our previous work [VAC7-9], [VAC10-11] were done with "(discrete and continuous time) chaotic oscillator [VAC7-9] and ring oscillator-based RNGs [VAC11-13]. These techniques should be made compliant with the use cases and generalised within the scope of the project. For instance, The C. Irreproducibility and D. Robustness tests have not been generalised to any true random number generation scheme. So, our plan is to generalise the 4-step vulnerability analysis (A-B-C-D steps) valid and applicable to all domains where cryptographic components are used.
- For Big Crush tests at least 1TB data is needed. Thus, this test can only be implemented over strong computers (e.g. work stations)
- [VAC1] K. Martin, Everyday Cryptography: Fundamental Principles and Applications, 2nd Edition, Oxford University Press,2017.
- [VAC2] S. Ergün, and S. Özoguz, Truly random number generators based on a non-autonomous chaotic oscillator, AEU-International Journal of Electronics and Communications 61, no. 4: 235-242, 2007.
- [VAC3] L.E. Bassham III, A.L. Rukhin, J. Soto, J.R. Nechvatal, M.E. Smid, E.B. Barker, S.D. Leigh, M. Levenson, M. Vangel, D.L. Banks, N.A.Heckert, Sp 800-22 rev. 1a. A statistical test suite for random and pseudorandom number generators for cryptographic applications, National Institute of Standards & Technology, 2010.
- [VAC4] G. Marsaglia, DIEHARD Statistical Tests: https://tams.informatik.uni-hamburg.de/paper/2001/SA_Witt_Hartmann/cdrom/Internetseiten/stat.fsu.edu/source.tar.gz,
- [VAC5] P. L'Ecuyer, and R. Simard, TestU01: A C library for empirical testing of random number generators, ACM Transactions on Mathematical Software (TOMS) 33, no. 4: 1-40, 2007.
- [VAC6] N.C. Göv, M.K. Mıhçak, S. Ergün, True random number generation via sampling from flat band-limited Gaussian processes, IEEE Transactions on Circuits and Systems I: Regular Papers 58, no. 5: 1044-1051, 2010.
- [VAC7] S. Ergün: Predicting the Secret Parameters of a Chaotic Random Number Generator from Time Series, In ICASSP 2019-2019 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), pp. 2547-2551. IEEE, 2019.
- [VAC8] S. Ergün: On the security of chaos based “true” random number generators, IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences 99, no. 1: 363-369, 2016.
- [VAC9] S. Ergün, and B. Acar: Revealing the Secret Parameters of an FPGA-Based “True” Random Number Generator, IEEE International Symposium on Circuits and Systems (ISCAS), 1-4, 2020
- [VAC10] B. Acar, S. Ergün: Correlation-based cryptanalysis of a ring oscillator based random number generator, 2018 IEEE 61st International Midwest Symposium on Circuits and Systems (MWSCAS), 1050-1053, 2018.
- [VAC10] B. Acar, S. Ergün: A Digital Random Number Generator Based on Irregular Sampling of Regular Waveform, 2019 IEEE 10th Latin American Symposium on Circuits & Systems (LASCAS), 221-224, 2019.
- [VAC11] B. Acar, S. Ergün: A Reconfigurable Random Number Generator Based on the Transient Effects of Ring Oscillators, IEEE Transactions on Circuits and Systems II: Express Briefs 67 (9), 1609-1613, 2020.
- [VAC12] R. Günay, S. Ergün: IC Random Number Generator Exploiting Two Simultaneous Metastable Events of Tetrahedral Oscillators, IEEE Transactions on Circuits and Systems II: Express Briefs 67 (9), 1634-1638, 2020.
- [VAC13] K. Demir, S. Ergün: Random Number Generators Based on Irregular Sampling and Fibonacci–Galois Ring Oscillators, IEEE Transactions on Circuits and Systems II: Express Briefs 66 (10), 1718-1722, 2019.
